Threat can be anything that can take advantage of a vulnerability to breach security and negatively alter erase harm object or objects of interest. A direct threat identifies a specific target and is delivered in a straightforward clear and explicit manner.

7 Types Of Cyber Security Threats
Data security is another inline threat under which your personal data is.

. Cyberattacks are increasing in sophistication and volume with many cybercriminals using a combination of different types of attacks to accomplish a single goal. Network-based threats are especially common and risky because cybercriminals can steal unencrypted data while people use public WiFi networks. Trojan horses spyware adware ransomware phishing viruses worms rootkits and browser hijackers are all types of malware.
Malware a portmanteau of malicious software is any software used to disrupt computer operation gather sensitive information or gain access to private computer systems. Malware is defined by its malicious intent acting against the requirements of the computer user and does. Malicious software comes in many forms such as viruses Trojan horses spyware and worms.
Modern technology and societys constant connection to the Internet allows more creativity in business than ever before including the black market. Trojan horse worms virus spyware are some of the different types of online threats. Email bombing is characterised by an abuser sending huge volumes of email to a target address resulting in victims email account or.
The era of online payment gateways has arrived and due to this a lot of payment frauds have also entered the scene. Mobile Device Security Threats. Anything that one downloads from the internet can have hidden malware inside.
Types of Threats Threats can be classified into four different categories. Though the list of potential threats is extensive below youll see the most common security threats you should look out for. Spyware collects information and sends it to the hacker.
Drive-by Attack A website is loaded with a malware and when a visitor happens to come across such a website their device is infected with the malware. A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. A virus needs a host program to run but worms can run by themselves.
After a worm affects a host it is able to spread very quickly over the network. Email bombing and spamming. Protecting business data is a growing challenge but awareness is the first step.
Physical threats to mobile devices most commonly refer to the loss or theft of a device. Mobile Network Security Threats. Direct indirect veiled conditional.
A Trojan horse or Trojan is a type of malicious code or software that looks legitimate but can take control of your computer. Information Security threats can be many like Software attacks theft of intellectual property identity theft theft of equipment or information sabotage and information extortion. The main threat can be of online frauds.
The malware will steal valuable data or crash the system. An indirect threat tends to be vague unclear and ambiguous. Different kinds of online threats.
Maharana Pratap- Download PDF Here Aspirants can find complete information about upcoming Government Exams through the linked article. Here are the top 10 threats to information security. Malware is usually picked up from the internet or through ones email.
Its purpose is to steal private information from a computer system for a third party. Cybercriminals are carefully discovering new ways to tap the most sensitive networks in the world.
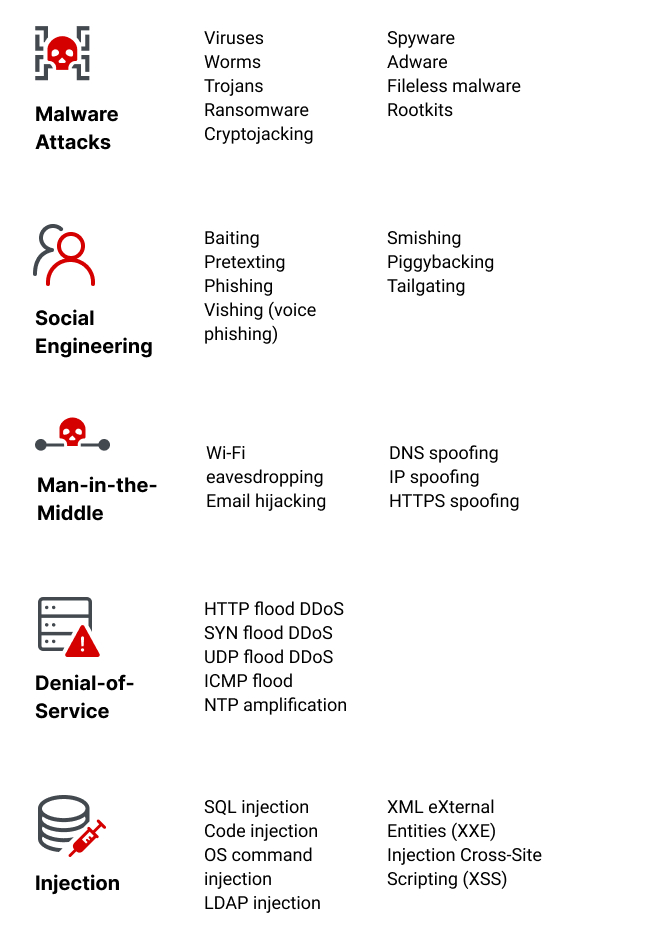
Cyber Security Threats Types Sources Imperva

0 Comments